Grinch-Networks CTF Writeup Flag 8
The Grinch thought it might be a good idea to start a forum but nobody really wants to chat to him. He keeps his best posts in the Admin section but you’ll need a valid login to access that!
Forum
The Forum was a very funny challenge. I got stuck in the middle and got an good push in the right direction after a long time of searching around. But lets see.
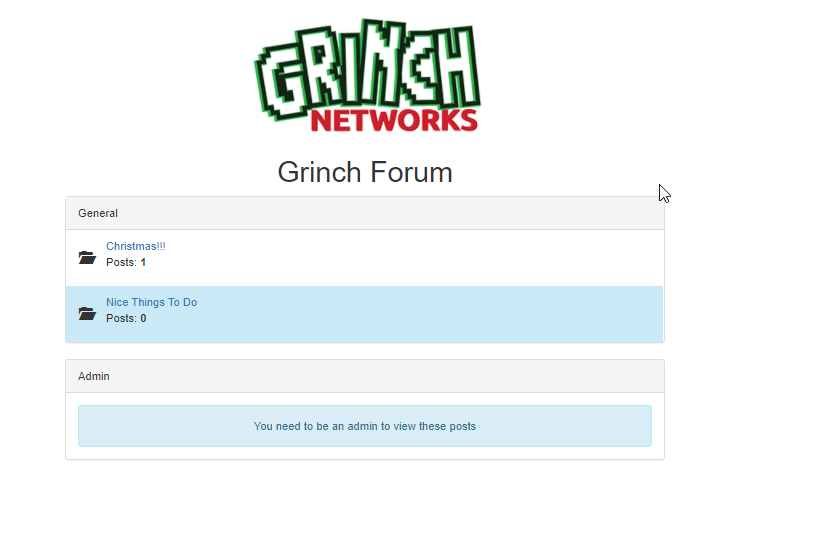
Lets start with analyzing what we can do with the application. We can click on categories. There is an admin section we can no see. Ok. There is a login button on the top right showing an login window.
There is one post in this category.
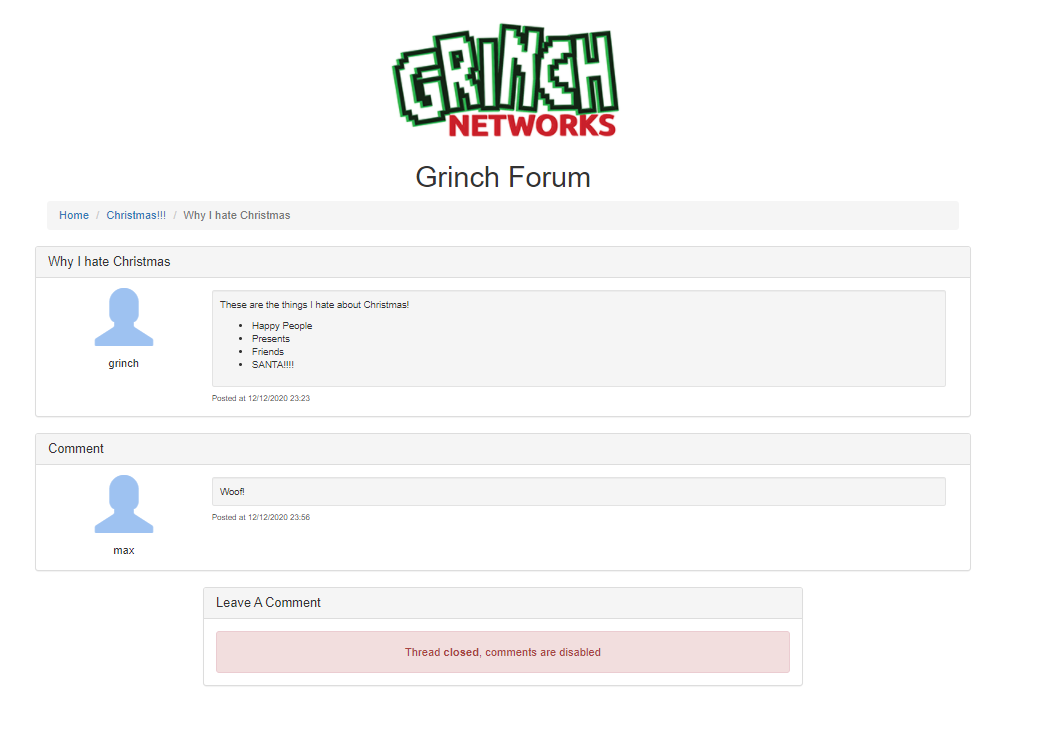
Ahhh a user grinch and max. Lets make a note about these two guys.
The page-source of all pages wasn’t helpful at all. Nothing!
Before I started bruteforcing the login I wanted to check the URLs.
https://hackyholidays.h1ctf.com/forum/1/1
It is worth trying if there are any other directories beside 1 and 2. With this shell command we can list the HTTP-Status code for the request we are sending with curl.
for i in $(seq 1 1 100); do curl -s -o /dev/null -w "%{http_code}" "https://hackyholidays.h1ctf.com/forum/1/$i"; done
Unfortunately nothing! No other post are available. So lets kick off dirb to find maybe some hidden directories.
Ohhh yesss! A phpadmin interface. But its also protected with a username and password.
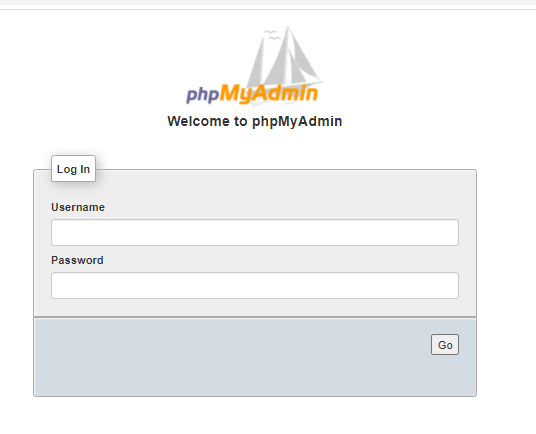
Database users are sometimes very random so bruteforcing usernames and passwords does not make any sense (you remember our 10K * 10K problem?) I have tried bruteforcing the password for the user forum as well as root. No success. I have used the same tool and settings as I explained earlier in this write-up.
Before I started the second brute force for the forum user / password using grinch and max, there was a message on the forum there is NO! bruteforce needed at all! So that was a dead end as well!
Whats next… There was no vulnerability. Got a hint on t
Do a google search on github
"Grinch Networks" site:github.com
Bingo: https://github.com/Grinch-Networks
After digging through the source code I have found the Db Model class:
https://github.com/Grinch-Networks/forum/blob/main/models/Db.php
Unfortunately there were no passwords BUT lets have a closer look on the first commits.
Bingo!! https://github.com/Grinch-Networks/forum/commit/07799dce61d7c3add39d435bdac534097de404dc
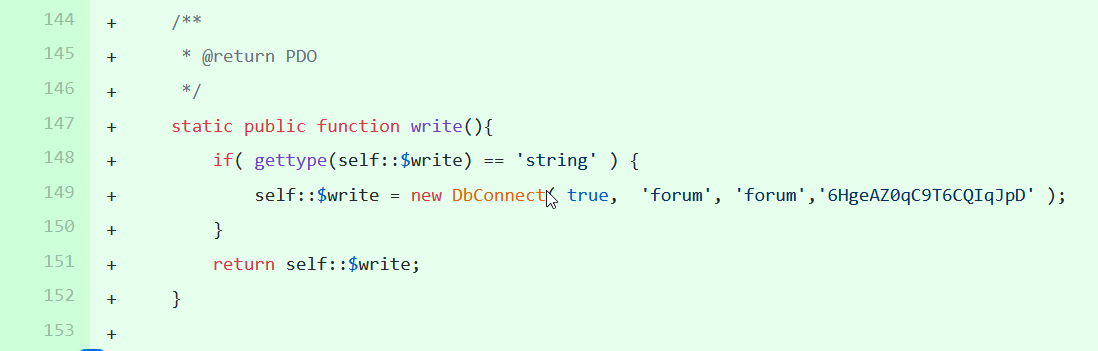
static public function write(){
if( gettype(self::$write) == 'string' ) {
self::$write = new DbConnect( true, 'forum', 'forum','6HgeAZ0qC9T6CQIqJpD' );
}
return self::$write;
}
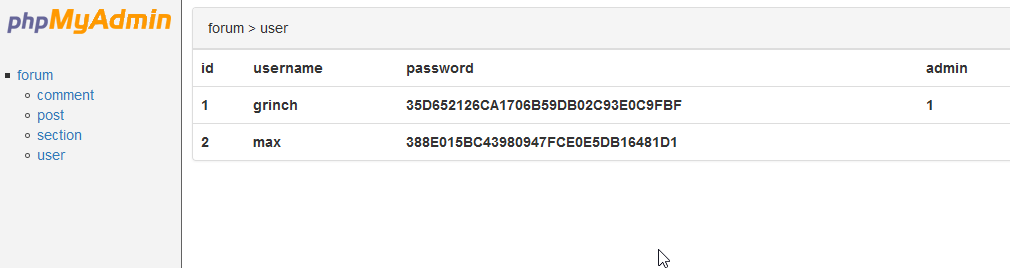
Lets Crack MD5. hashcat was not successful. Lets try online resources:
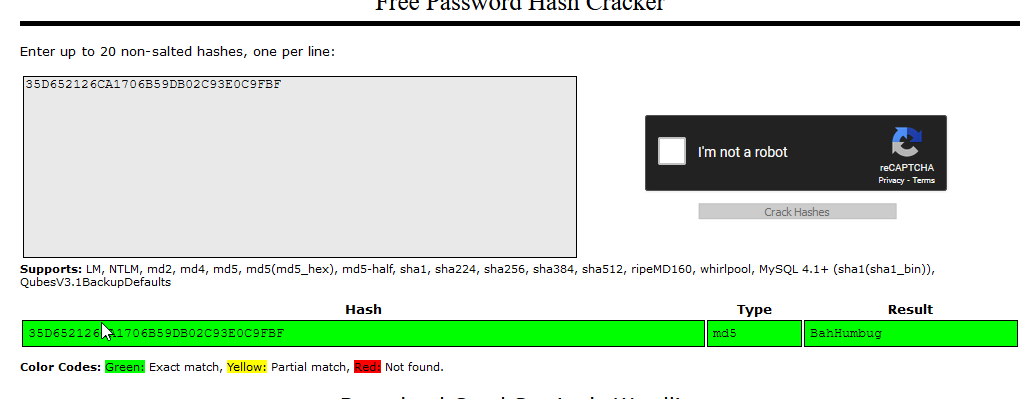
With this password I was able to login.
flag{677db3a0-f9e9-4e7e-9ad7-a9f23e47db8b}
Lets move on with Challenge 9.